Logical volume manager (LVM)
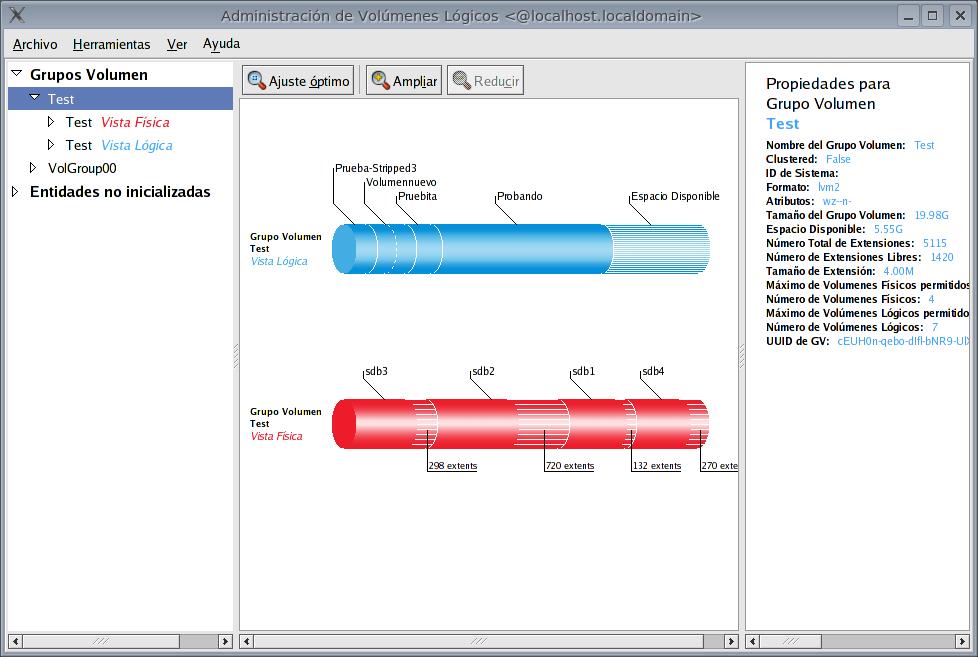
Introduction LVM are the initials for Logical Volume Manager, a powerful tool present in actual Linux systems inspired in the implementation available in other systems like AIX and HP-UX. LVM introduces a separation between system structure and elements like disks, partitions, filesystems to which we are used to. LVM has three levels: Physical volumes Volume Groups Logical volumes One of the benefits of LVM over traditional systems is that LVM introduces an abstraction layer which improves the limitation of a disk, allowing us to have a filesystem to span over several disks, resizing thus making a more efficient usage of storage. ...